Understanding Risk Management

Computerized systems have become a part of almost every aspect of laboratory activities and regulated companies are, therefore, making great efforts to raise their level of compliance with both the regulatory requirements and the expectations of governing agencies. However, companies often end up creating quality systems and mechanical processes that are too rigid for efficient Computer Systems Validation (CSV). This limits their ability to practice the more modern and FDA preferred risk-based compliance methodology. A risk-based compliance methodology delineates clear responsibilities, processes, and documentation requirements that increase the level of compliance while generally reducing the CSV effort and cost.
The following illustrates one example of a well-defined Quality Risk Management approach:

Risk Identification & Assessment
Applying a Quality Risk Management process during the initial stages of a CSV project allows companies to identify and assess the potential risks for each area of system functionality. And per FDA guidelines, the scope and extent of validation efforts should be based not only on quality risk but also on software complexity, as complexity increases the likelihood of future failure. These factors can be used to prioritize and provide focus to your software validation testing and documentation efforts which is the ultimate objective of a risk-based CSV approach. Happily, a bonus to prioritization and focus is generally a reducing in overall CSV effort and CSV project cost.
To prioritize and attain focus, three fundamental questions should be answered for each risk:
- What might go wrong (risk)?
- What is the likelihood (probability) that it will go wrong?
- What are the consequences (severity) of it going wrong?
Additional Reading: Lab Informatics System Risk Assessment – Done! Now What?
Risk Control
A well-documented Risk Assessment also encompasses the decisions made to mitigate the probability and severity of each risk. The amount of effort applied to risk control should be proportional to the significance of the risk.

Thus the following two questions are the focus of risk control:
- What can be done to reduce or eliminate risk?
- What is the appropriate balance among benefits, risks, and resources?
Risk control mechanisms are applied throughout the system life cycle. The following table provides some examples:
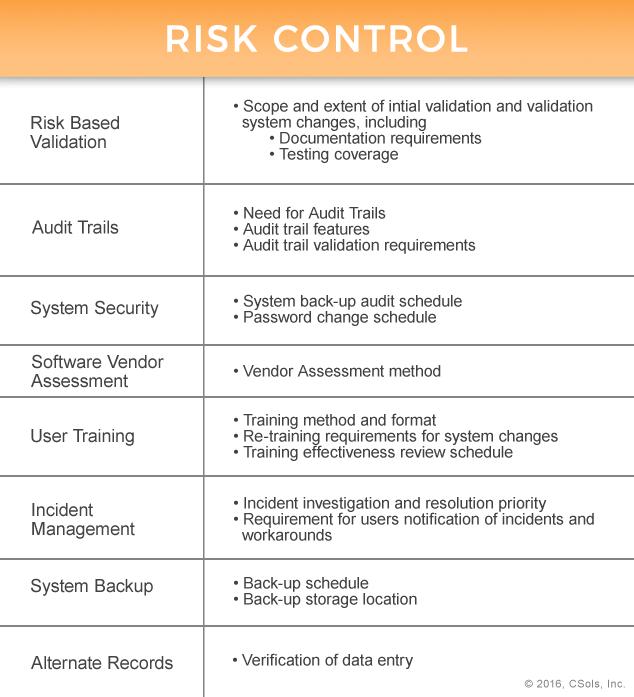
Even after risk control mechanisms are applied some risk remains. This residual risk can either be accepted or further reduced, but whatever your organization’s decision, the residual risk should be documented as part of the assessment. Throughout the lifecycle of the computerized system, the risk assessment should be periodically reviewed and maintained.
With computerized systems being endemic in the laboratory environment and becoming increasingly more complex, the utilization of them in regulated environments imposes various degrees of risk to both the regulated product and the associated records. It is important to understand that all risks should be identified and managed throughout a system’s lifecycle. An effective Quality Risk Management approach not only ensures the quality of the system during both the development and production stages, but also provides a framework for decision making should a quality issue arise. It further provides a structured and robust approach to ensuring the functionalities with the highest risk receive the requisite concentrated validation effort. By utilizing a Quality Risk Management process that incorporates a risk-based approach, your CSV projects will yield confidence that Product Quality, Patient Safety, and Data Integrity will attain and maintain the highest level.

How has your organization evaluated risk? Do you feel like you have a thorough risk management plan?
Comments